It’s been a big year for bridges and the cross-chain ecosystem as a whole, in good and bad ways. As the year comes to an end, it’s time to reflect on the significant events from the cross-chain world that burnt some bridges but, more importantly, built new ones.
Let’s dive in!
January
Cross-Chain or Multi-Chain? The Debate
Before any of the infamous bridge hacks, Vitalik raised concerns over the fundamental security limits of bridges and argued, “the future will be *multi-chain*, but it will not be *cross-chain*”.
While bridges are now used to move billions of dollars every day, Vitalik’s argument rings true in many ways:
It’s always safer to hold native assets — assets are always safer when retained on their native chain rather than being bridged and wrapped into an asset on a chain where they don’t belong, as highlighted by the $326M Wormhole hack in Feb 2022. In this case, wrapped ETH on the Solana side of the bridge became unbacked due to the hack as 120k ETH were exploited on the Ethereum side.
Bridging is more relevant in zones of sovereignty as opposed to inter zones — From the graphic below, we can see that bridging in large volumes is more relevant across a specific zone of sovereignty. For instance, within the EVM ecosystem, between top chains like Ethereum, BNB Chain, Polygon, Arbitrum, Avalanche, Optimism, etc., or within the Cosmos ecosystem or between Polkadot relay chain and parachains (like Acala) within the Polkadot ecosystem.

While it’s possible to bridge from Ethereum to Solana or the Cosmos ecosystem, it can be seen that 1) these routes are not being utilized at the moment and 2) there are very few bridge providers that offer these routes (Axelar for Cosmos <> EVM and Wormhole for Solana <> EVM connectivity). However, as bridges become more robust in the future, this trend could likely change, and the flow of value across zones becomes more popular.
Read of the Month
In crypto, we love analogies that help us make sense of the madness. In Jan, Haseeb Qureshi (Managing Partner @ Dragonfly) dropped one of the best pieces of writing of 2022 that provided a mental model to help us understand how the multi-chain ecosystem is evolving.


February
The First of Many Bridge Hacks
In February, the bridge industry experienced its first major hackin the $322M Wormhole exploit that took place on Feb 2, 2022, the second-biggest hack in the history of the DeFi at that time.
Here’s what happened:
The attacker managed to exploit a signature verification vulnerability in the Wormhole Network. This allowed them to mint 120k wETH on Solana, which was not backed by ETH deposits on Ethereum. As a result, the hacker was able to bridge 93,750 ETH back to Ethereum based on fake whETH holdings. The hacker was also able to liquidate ~36K wETH on Solana into USDC and SOL.
This hack was critical as it highlighted many things about bridges and how the year might unfold for them:
It showed that bridges are in their nascent stages of development, and unfortunately, we would likely see more exploits in the near future.
While not all bridges are built equally, this hack occurred because of a smart contract exploit. Since everything in crypto runs on smart contracts, this could’ve happened to any bridge, as they are all susceptible to bugs in smart contract code.
Read of the Month
With the help of LI.FI, Ethereum.org, a public-goods knowledge portal maintained by the Ethereum foundation, dropped an introduction to bridges that covered:
What are blockchain bridges
Why do we need bridges
Bridge use cases
Types of bridges
Risks of using bridges


A great intro to bridges, especially for beginners, and one that also made it to our bridge survival guide!
March
The Need to Build Secure Bridges, Say No to Single Digit Validator Sets.
New month, new bridge hack… but this time, the hack raised concerns over the fundamental design of certain bridges (externally verified). In March, Ronin Network, Axie Infinity’s sidechain, was hacked for more than $625M — 173,600 ETH and 25.5M USDC, currently the biggest hack ever in crypto.
Before Ronin, we had witnessed Wormhole, where a smart contract was exploited to print fake whETH on Solana. While that hack was significant, its cause could’ve taken down any smart contract-based product, and thus the reason behind the hack was not specific to bridges. With Ronin, however, things were different. The hack took place at the root of trust of the bridge, i.e., the validator set, which could have potentially been avoided with a different, more trust-minimized bridge design and architecture.
Here’s what you need to know about the Ronin bridge design and how the exploit took place:
At that time, Ronin Bridge was a 5-of-9 validator bridge. This means that out of the 9 validators, it required 5 to act honestly to validate transactions and allow funds to move across chains.
5 of the keys were compromised via a backdoor in the Ronin Bridge node when the exploit occurred.
The attacker managed to gain access to the private keys of 5/9 validators (4 Sky Mavis Members and 1 from the Axie DAO node) and thus was able to move the funds.
Once 5 private keys were compromised, the attacker could take all funds from the bridge.
This hack raised concerns about the fundamental security of bridges and put forward several important lessons for the entire industry:
Focus on trust minimization is vital – The Ronin Network relied on a validator-based bridge. Such designs have a fundamental security assumption that the validators’ private keys cannot be compromised. While validators can work, it’s necessary to set up engineering practices to maintain security and ensure trust assumptions are not exploited.
Need for improved monitoring measures — The exploit was only noticed 6 days later when a user tried to withdraw but couldn’t. This suggests the Ronin bridge didn’t have automated monitoring measures to alert them in such cases.
Read of the Month
An interesting read from Arjun Bhuptani (Founder @ Connext) that talks about building secure bridges and moving away from trusted bridge designs like Ronin. This piece dives deep into the design mechanics of a new flavor of bridges – optimistically verified – that introduce a new trade-off: latency, changing the interoperability trilemma into a quadrilemma.


April
Neither Cross-Chain nor Multi-Chain, Omnichain is the Way for NFTs
Moving away from the bridge hacks, let’s look at some innovations, of which there were plenty throughout the year. In a year that saw previously chain-specific NFT Marketplaces like Opensea (Ethereum) and Magic Eden (Solana) add support for NFTs on other chains, an evolution of bridges known as Arbitrary Messaging Bridges (AMBs) took NFTs to another level by making it possible to deploy them on multiple chains.
Gh0stly Gh0sts and LayerZero have started a new trend — Omnichain NFTs
Omnichain NFTs are chain-agnostic, i.e., NFTs that live on multiple chains. Until then, all we had were NFT collections native to one chain, or even if an NFT were available on multiple chains, projects would lock the NFT on the source chain and mint a new one on the destination chain. However, because Gh0stly Gh0sts was built on LayerZero, an AMB, they could be transferred to/from any chain supported by L0 like Ethereum, BNB Chain, Arbitrum, Polygon, and Aptos, among others. As a result, Gh0stly Gh0sts NFTs support natively omnichain NFTs — it burns the existing NFT on the source chain and mints it on the destination chain.
The ability to mint native NFTs on different chains was something truly different at the time and opened new possibilities for NFTs in the cross-chain ecosystem.
Read of the Month
The term ‘trustless’ is thrown around a lot when it comes to describing bridges. Unfortunately, it was often used as marketing material and doesn’t do justice to the reality. This article attempts to define the term ‘trustless’ in the context of bridges and also measures the level of ‘trust’ required by various bridge designs.


May
May the Force be With Optimistic Bridges
In May, Rainbow Bridge (Near <> Ethereum) was attacked, but the attacker failed and lost 2.5 ETH in the process. The bridge’s security architecture prevented the attack automatically — Rainbow Bridge watchdogs flagged and challenged a fraudulent block. This stopped the attack and ensured user funds were safe, making everyone optimistic about the future of bridges and their security.
Rainbow Bridge is a light client bridge going to Near and an optimistic bridge going to Ethereum. Here’s what happened during the attack:
Independent watchdogs in the Rainbow bridge architecture responsible for monitoring NEAR headers and flagging/challenging any headers with invalid signatures (malicious intent) caught a malicious transaction and challenged it.
Since anyone can become a watchdog, one MEV bot front ran the watchdog’s challenge to gain 2.5 ETH and succeeded. This rolled back the fabricated block of the attacker, and the attack was stopped. The attacker lost 2.5 ETH, which was paid to the MEV bot.
As a result, even though the bridge got attacked, the fraud proofs submitted by watchdogs on an optimistic bridge saved users from losing funds and prevented a potentially billion-dollar attack.
Read of the Month
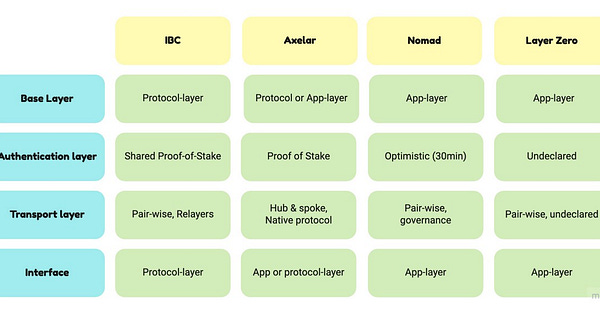
A good read that offers a framework for understanding AMBs and assessing their security in Part 1 and Part 2 applies those ideas to AMBs like IBC, Nomad, LayerZero, and Axelar, providing an overview of the different types of AMBs.

June
Another Bridge Hack on the Horizon?
Unfortunately, this month was marred by another bridge hack. This time, it was Harmony’s Horizon Bridge, a native bridge that took down an entire ecosystem with it.
On June 24, 2022, Horizon Bridge, which links Harmony with Ethereum and Binance Chain, was exploited for $100M. The team found that private keys were compromised, leading to the breach of Horizon Bridge, with funds being stolen from the Ethereum side of the bridge. The hacker swapped $100m in altcoins for ETH.
Since the hack, almost all the TVL in Harmony’s DeFi ecosystem has been wiped out and is currently less than $50k. This hack highlighted how crucial native bridges can be to an ecosystem and what their contagion effects could look like in case of hacks like the one suffered by the Horizon bridge.
Read of the Month
This is an excellent article on AMBs, the title of which mocked ‘The Bridges Are Dead, Long Live The Bridges!’ given all the bridge hacks.


July
Are we Optimistic about App-Chains?
In July, we witnessed an event combining some of 2022’s biggest trends – app-chains, bridges, and optimistically verified systems. Yes, we’re talking about the announcement of Synapse Chain!
On July 28, 2022, Synapse Protocol announced Synapse Chain, a novel smart contract execution layer built atop Synapse’s generic cross-chain messaging system and value bridge. Notably, Synapse Chain uses an optimistic verification design to verify cross-chain messages, switching from an externally verified, multi-sig design.
Read of the Month
By now, we had many articles about bridges, but this was the first one that discussed the business model of bridges and explained how they actually make money!


Notably, in July, L2Beat provided a comprehensive framework to evaluate the security of different types of bridges.
August
The Rise and Fall of Optimistic Bridges
August was another bad month for bridges as we witnessed one more bridge hack, which made us all question what the future of bridges might look like.
On August 2, 2022, Nomad Bridge was exploited for $190M, making it the 5th largest exploit in the history of DeFi. The exploit occurred because of an implementation error during a routine upgrade where the Nomad team marked the zero hash as a valid root. This allowed hackers to spoof messages on Nomad and drain all the funds (read more here), and Nomad’s TVL went to 0.

Some of the funds were recovered by whitehat hackers and returned to the Nomad team — $32M+ from 86 wallets (these funds are now being distributed among the affected users).
This hack highlighted how bridge hacks could have tremendous contagion effects on the ecosystems that rely heavily on them. For instance, Moonbeam, Milkomeda, and Evmos relied on Nomad as their go-to canonical bridge, and because of the hack, massive amounts of funds were bridged away from these chains.
Read of the Month
If there’s an article that made sense of all the madness in the bridging niche, it was this one! A snapshot of the ecosystem in Q3 2022 that offers an updated version of the bridge bible.


This month had several other great articles that we must mention:
Assessing Blockchain Bridges by Joel John
Security Stack-Up: How Bridges Compare by Jump Crypto
September
Controlling the Narrative in the Multichain Ecosystem
September saw Circle announce the Cross-Chain Transfer Protocol (CCTP) to support USDC interoperability for developers & their users, a move that enables the movement of USDC across chains natively.
To understand the goal behind the launch of CCTP, we need to look at how USDC currently moves across chains. To move USDC cross-chain, it is required to be locked on one chain and minted on another, “creating fragmented liquidity and a complicated user experience.”
Cross-Chain Transfer Protocol simplifies the flow of liquidity and improves the user and developer experience by enabling USDC transfers natively across chains, i.e., without locking it on one chain and minting a wrapped version on the other. According to Circle, “Cross-Chain Transfer Protocol effectively teleports USDC from one ecosystem to another, maximizing capital efficiency and streamlining the user experience.”
In a similar move earlier in 2022, we saw MakerDAO discuss its ’Multichain Strategy’, which stated how Maker needed its own bridge to truly capture the value of DAI across ecosystems and also control the narrative around the DAI brand. As a result, MakerDAO launched Maker Teleport, an infrastructure for teleporting Canonical DAI across the multi-chain space.
Once both Circle’s CCTP and Maker’s Teleport are live and integrated across cross-chain protocols, it would be interesting to see how the dynamics change regarding speed and time when it comes to bridging USDC/DAI as compared to the widely used liquidity networks at the moment.
Read of the Month
A comparison framework to understand and analyze the most critical infrastructure in crypto, arbitrary messaging bridges aka AMBs!
This article gives an overview of the security trade-offs made in the cross-chain space so that developers can quickly assess the pros and cons of building on a particular AMB. It explores the design, security, and trust assumptions of eight data messaging bridges: LayerZero, Wormhole, Nomad, Celer Inter-chain Message (IM), Multichain’s anyCall, Hyperlane (previously Abacus), deBridge, and Axelar. Moreover, it compares these eight bridges using an evaluation matrix.


October
Hack We Go Again (BNB Edition)
This was hopefully the last bridge hack of the year. This hack could’ve been the last straw for bridges, but surprisingly, its effects were not felt too much. However, things could’ve easily been very different.
On Oct 7, 2022, the BSC Token Hub, the native cross-chain bridge between BNB Chain and BNB Smart Chain, suffered a $586M exploit, making five of the six largest hacks in DeFi history related to bridging – with the total amount of funds lost amounting to over $2 billion. The attacker stole 2 million BNB tokens in two transactions and escaped with roughly $110 million in value spread across Ethereum, Fantom, and other EVM-compatible chains.
The BSC Token Hub hack put many things into perspective related to bridge security (specifically w/ light clients). More importantly, it prevented another multi-billion hack that would’ve wreaked havoc over the entire Cosmos ecosystem and destroyed trust in the bridges forever…
Here’s what happened:
After the BSC Token Hub hack, the core developers of Cosmos and Osmosis ramped up security audits for IBC and discovered a critical security vulnerability. This is because there are many overlaps between Binance Bridge (BNB Beacon Chain <> Smart Chain) and IBC, especially in how the two bridging mechanisms utilize light clients:
Forged merkle proofs in light clients – In Binance Bridge’s case, a hacker forged a merkle proof. This should technically not be possible as merkle proofs are highly secure. However, as highlighted by the BNB Bridge hack, ensuring the integrity of IBC’s merkle proofs is essential, given that IBC relies heavily on them for its functioning.
The hack was caused due to a vulnerability in a core Cosmos repo – Binance is one of the most significant users of Cosmos’ software. It was built on top of Cosmos’ repo and thus inherited the vulnerability, which was eventually exploited during the hack. IBC only managed to avoid a hack as its newest implementation (IBC-GO) uses a different library (from the one used by Binance) for proof verification.
This meant, if Binance's light clients could be hacked, IBC, one of the most secure bridge implementations, could’ve been exploited too. However, this was avoided, thanks to the alertness and quick execution of Comsos devs that resulted in a quick patch for all major IBC support chains.
Read of the Month
Karthik Inbasekar’s article on “Bridging the Multichain Universe with Zero Knowledge Proofs”, has many people discussing the future of bridges and the use of ZK tech to improve their security.
Given the complexity of zk-tech and bridges, whether zk-tech will reduce bridge hacks still remains to be seen, as most bridge hacks have occurred due to implementation errors. This article provides a comprehensive overview of the projects currently working to bring zk-tech to bridges.


November
It’s Essential to Have Good Tools
Until November, we didn’t have many great resources and tools for bridging data and cross-chain information. However, things changed big time in November as DeFiLlama released their bridging dashboard, and CryptoStats came up clutch with a new info site called CryptoFlows.com!
The Bridge Dashboard
If you thought liquidity in the crypto ecosystem was fragmented, wait till you explore bridge analytics. To address this pain point, the Llamas introduced a new product: the Bridge Dashboard!
In its current state, the Bridge Dashboard covers 12 EVM-chains, 21 bridges, and provides bridge analytics such as bridge volumes (24h, 7d, 1mo), large Transactions (via x bridge, deposit/withdrawal, token, value), and total inflows for chains and movement of assets across chains.
CryptoFlows
CryptoFlows.com is a visualization tool offering the complete map of the ecosystem: charting the relationships between all major chains, and the bridges that connect them together. It offers:
Top exporters and importers — a list of chains ranked by the total value they export and the total amount of value they import.
Bridge view — that shows omnidirectional links representing individual bridges.
Bridge security — insights on important bridge security information, such as security assumptions and the total bug bounties.
Read of the Month
Building on the ‘With Bridges, Trust is a Spectrum’ article earlier in the year, LI.FI provides a quantified framework for classifying bridges on the scale of trustlessness from very low to very high and lists some of each bridge's key security assumptions.


December
A Glimpse of What’s in Store; Innovating Through EIPs
Ethereum Improvement Proposals aka EIPs, are forum posts that bring the community together. Here we find the community brainstorming on cool ideas that initially sound too good to be true but thanks to the giga brains in crypto, gradually move from concept to proposal and are finally executed for the betterment of the entire space. Currently, there are two such active EIPs in the cross-chain space:
EIP–5164: Multichain Governance
Originally proposed as a solution for multichain governance, EIP-5164 has transformed into a specification to define a generalized cross-chain execution interface for cross-chain contract calls for EVM-based blockchains.
In essence, EIP-5164 attempts to mass-produce a solution that would allow dApp token holders to vote and approve state changes across multiple chains – meaning 1) tokens should be able to vote from any chain and 2) whatever changes are approved by the vote automatically get executed on the various EVM-compatible iterations of a dApp like PoolTogether.
A secondary, but perhaps more important, facet of EIP-5164 is its potential to improve code reuse and how it might make it easier to interact with bridges in the EVM-blockchain space. In the current state of bridging in the EVM-world, each bridge has different APIs and brings differing degrees of trustlessness to the table, making it rather messy to interact with multiple bridges (LI.FI is a bridge aggregator, we feel this).
EIP-5164, as a common specification, could potentially allow for a more generalized way for dApps and projects to interact with bridges.
EIP-6170: Cross-Chain Messaging Interface
EIP-6170 aims to make it easier for developers to tap into the different options available in the AMB space by offering a standardized interface to interact with the different AMBs.
In essence, this EIP focuses on how messages (state) should be sent and received across chains using a specific standard since, at the moment, different AMBs use different interfaces resulting in “unnecessarily complex competing implementations”. Thus, through this EIP, the plugin layer for these AMBs can be standardized, reducing the complexity of building a cross-chain dApp.
Read of the Month
An interesting read that touches on a critical area of research regarding bridge security: finality. The article gives a general and formal definition of finality means for different chains. It offers insight into how bridges must navigate these challenges to ensure the security of users’ funds.


Closing Remarks
It’s been a topsy-turvy year for bridges. However, despite all the turmoil, there’s still hope, and we’re optimistic about the future of bridges and the cross-chain ecosystem. Bridges are still in their nascent stages of development and with each passing day, they are becoming more secure and battle-tested. Moreover, the bridge builders are still here, striving to make the cross-chain space safer and easier to navigate.
A few things to lookout for in 2023:
ZK powered bridges – how do we leverage zk technology to build safer bridges?
Optimistic bridges – do people stick with this design despite the complexities in implementing them, as highlighted by the Nomad hack?
App-chains – how do they solve the bridging problem to onboard users easily?
Despite the fundamental security concerns, do validator-based bridges still have a place in the bridging niche? How do teams decentralize the validator sets?
Will bridging stay concentrated between zones of sovereignty, or will an Axelar/Wormhole make bridging across zones a common practice?
Do bridge aggregators gain more dominance over individual bridges?
Bridges an infrastructure tool – do more dApps integrate bridges (either individually or through bridge aggregators) to abstract them away from the users?
Bridge hacks – do we see more/less of them in 2023?
Will we see any innovation in the design space of bridges through new approaches?
Cross-chain or multi-chain – will we get a definitive answer in 2023?
How do cross-chain protocols like Circle’s CCTP and MakerDAO’s Teleport change the way leading stablecoins like USDC/DAI move across chains?
All in all, it was a tough year for everyone. A year full of hacks, rugs, market downturns, and macroeconomic concerns. But, If you’re still here with us, stick around and build/learn through the bear, and we might just make it :)
Get Started with LI.FI Today
To learn more about us,
Head to our link portal at Link3.to/lifi
Read our SDK ‘quick start’ at docs.li.fi
Join the official Discord server
Follow our Telegram Newsletter
or try our any-2-any swaps NOW at transferto.xyz