Introduction
The last few weeks in the bridge world have been interesting, to say the least. Bridges went from being in the news for all the right reasons to being the reason why people just can’t trust crypto.
Let’s start with the good – we saw one of the biggest bridges in Synapse introduce V2, shifting from multi-sig to optimistic verification. Post the announcement, all we could talk about at LI.FI was how secure optimistic bridges are and how they might just be the future of bridges.
However, as it happens in crypto, the moment you get comfortable and things seem straightforward, something happens that shakes you up and makes you question everything you’ve believed until then. In this case, it was the 190+ million Nomad bridge hack, the 5th largest hack in the history of DeFi.
It’s been 2+ days since Nomad, an optimistic bridge considered to be one of the most secure designs in the ecosystem, built by some of the smartest brains in the bridge world (some of whom have been working in bridges for five years), got hacked. Many were quick to assume that the hack took place because of Nomad’s optimistic design. However, this could not be further from the truth. As it turns out, the hack happened because of a bug in the smart contracts, which was introduced during a regular upgrade. Thus, it was an implementation bug that led to the downfall of Nomad and didn’t have anything to do with bridge design.
Why We're Still Optimistic About Optimistic Bridges
Here are some design benefits of optimistic bridges over other bridge designs that make us believe that despite recent events, if implemented correctly, optimistic bridges might still be the future of bridges. (Editor’s note: when speaking of “optimistic” systems in crypto, be they bridges or rollups, it means that all transactions are considered to be true… until a validator/watcher proves otherwise)
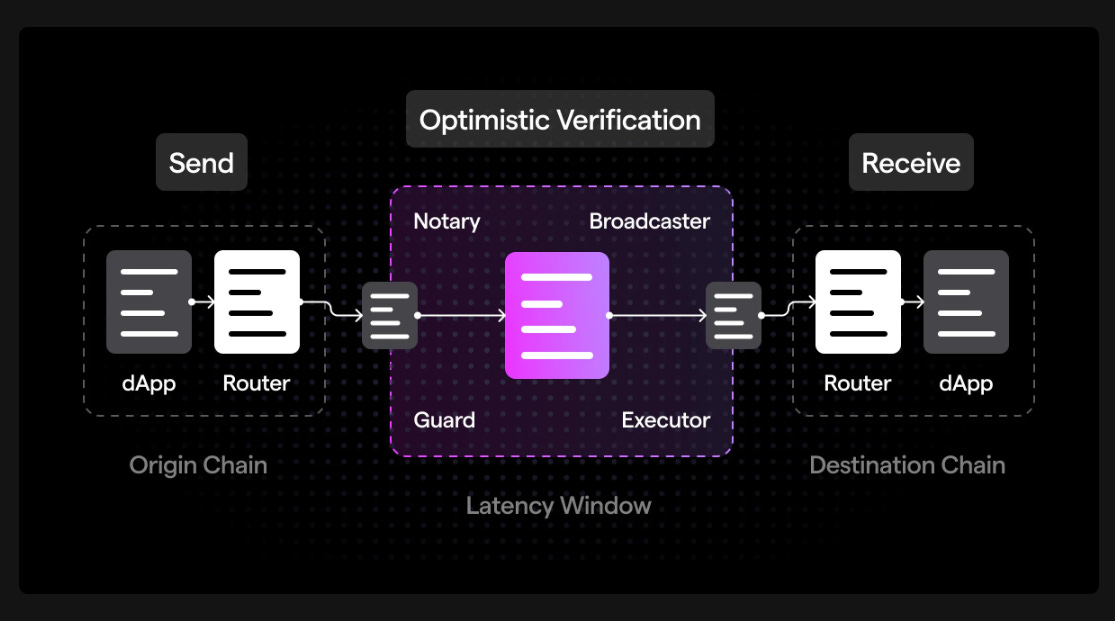
Minimal Trust Assumptions – Optimistic bridges introduce a latency tradeoff as they have a challenge period where watchers observing the system can flag fraud. Such a design requires them to only have a single honest verifier assumption (1 of n watchers to correctly verify updates) to ensure funds are not lost. Moreover, optimistic bridges do not claim to magically remove the third party from a bridging system. Instead, they embrace and minimize trust by distributing it to participants in the design, such as updaters and watchers (or watchdogs), and incentivize them to operate honestly.
Unbounded cost of attack – Optimistic bridges make it significantly more costly for bad actors to conduct an attack. They borrow from the design mechanism of optimistic rollups, where submitting fraud proofs within the optimistic window disallows any fraudulent transactions. As a result, the cost to attack the system becomes unbounded since there is no way to be sure that the fraudulent transactions will not be disputed by a single honest watcher via fraud proofs.
1 of N security model – Collusion between validators or private key compromises are not attack vectors with optimistic bridges because the watchers and fraud proofs in the design have a single honest verifier assumption. This means that an optimistic bridge cannot be compromised as long as there is one honest party in the system that can correctly verify the updates.

Safety over liveness – Optimistic bridges trade-off liveness (the guarantee that the system will provide data constantly and cannot be shut down) for security. They work similarly to an asynchronous network model where messages are not guaranteed to arrive at the end of a certain period of time. This asynchrony ensures that security can be maintained. In a way, they offer a circuit breaker that can halt the system to protect user funds. As a result, for optimistic bridges, the worst-case scenario is a system halt and not the loss of funds.
Now, let’s take a look at some of the bridges leveraging the benefits of the optimistic design. Here’s a mix of some old and new age bridges/interop protocols that use optimistic verification:
Rainbow Bridge
A bridge between Ethereum and Near, the Rainbow Bridge has adopted an optimistic approach for transactions going back to Ethereum from Near. In this system, the NearOnEth client (NEAR light client in Solidity as an Ethereum contract) verifies everything in the NEAR header. However, the signatures are not verified, and anyone can challenge them within a 4-hour challenge window. Watchdogs monitor submitted NEAR headers and challenge the ones with invalid signatures. As a result, even if a fraudulent header is verified by the NearOnEthClient, watchdogs can challenge them and prevent hacks.
Rainbow bridge’s optimistic design has already proven its security. On May 1, 2022, an attack on the Rainbow bridge was stopped automatically because of the optimistic architecture of the bridge as watchdogs came to the rescue.

Across
Across leverages UMA’s Optimistic Oracle (OO) to verify that relayers in the system have successfully filled a particular transaction. Relayers front liquidity to users and are reimbursed for their service by Across once the proof of relay and the validity of the original deposit is verified. Relayer reimbursements are verified through a two-step escalation game. The OO’s optimistic design accepts reimbursements as valid if they are not disputed within the challenge period of 2 hours. If there is no dispute, the relayer receives a reimbursement plus a reward, and if there is a dispute, then the dispute gets escalated to and resolved in 2 days by the UMA DVM, which is based on Vitalik’s SchellingCoin data feed. (Editor’s note: This description has been revised to reflect updates that recently occurred Across V2)
Synapse V2
In their recently launched V2, Synapse introduced an optimistically verified security model for cross-chain messages. Like Rainbow’s watchdogs, Synapse has Guards for observing cross-chain messages and submitting fraud proofs when they detect a malicious state update. Additionally, Synapse’s optimistic verification model uses the SYN token to provide economic security to the system and incentives to all the actors.
Nomad
Nomad is an interoperability protocol for sending arbitrary messages between blockchains. It uses an optimistic verification mechanism where honest participants, known as Watchers, can submit fraud proofs to dispute fraudulent transactions. Nomad’s optimistic design accepts transactions as valid if they are not disputed by Watchers within the challenge period of 30 minutes.
Beamer
Beamer is a trust minimized rollup bridge solution. It has a dedicated focus on inter-rollup bridging to solve the problem of rollup silos in the Ethereum ecosystem. The protocol is designed optimistically and has a 1 of N honest participant assumption, just like all the other optimistic bridges.
Honest participants in Beamer’s design can dispute the validity of the claim by liquidity providers that they have rightfully filled the transaction. Claims that are not disputed are assumed to be true. However, disputed claims lead to a challenge game where the validity of the claim is optimistically determined by the participants outbidding each other with increasing stakes. After the challenge period ends, the participant with the highest bid wins the challenge and the stake, and Beamer accepts the outcome of the challenge winner.
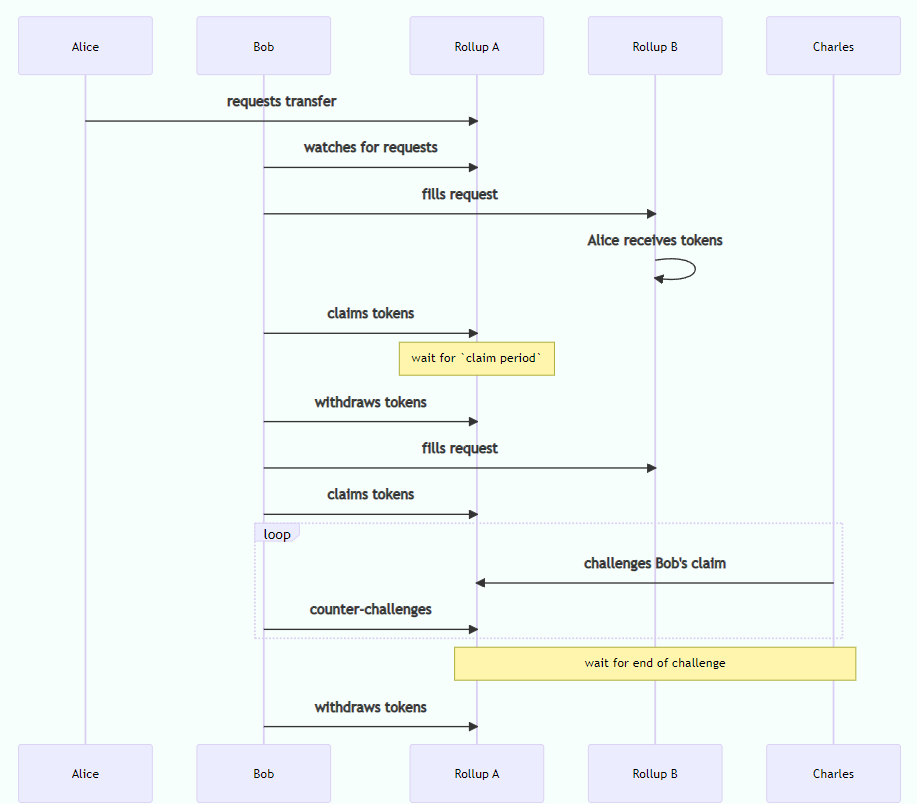
Moreover, the LP or the Challenger can settle the dispute on L1 at any point in time and avoid the escalation game. Thus, it can be said that Beamer can always fall back on Ethereum L1 to settle any dispute correctly.
Closing Thoughts
Despite the recent hack, optimistic bridges are still fundamentally one of the more secure ways of building bridges that strive for trust minimization. Thus, we believe that the future of bridging might still be optimistic and are excited to follow the progress of these incredible projects.
Get Started with LI.FI Today
To learn more about us,
Head to our link portal at links.li.fi
Read our SDK ‘quick start’ at docs.li.fi
Join the official Discord server
Follow our Telegram Newsletter
or try our any-2-any swaps NOW at transferto.xyz








thanks, so helpful